Updates to Our Ad Transparency, Efforts, and Findings
FunCorp is fully committed and continuing its focus on providing ad transparency. In November 2020, we responded to an article published by Pixalate. As we previously noted in our blog post, we strongly disagree with the assertions and conclusions stated in Pixalate's article. After conducting our internal investigation, findings from our third-party experts, and soliciting feedback from our ad partners and clients, we have found essential inconsistencies and discrepancies between the article's allegations and how iFunny functions. These findings further confirm that iFunny did not and could not generate the purported fraudulent ad traffic.
Before explaining our findings, we want to highlight a few critical notes. First, iFunny is not an advertising network. Instead, it makes available inventory that advertisers can buy through third-party SDKs. Second, iFunny works only with the intermediaries identified in our app-ads.txt. No other sellers are authorized to sell ad impressions for our traffic, and we do not control the ad creative passing through those intermediaries. Third, iFunny takes user privacy very seriously and fully complies with local laws, including CCPA and GDPR. Our privacy practices are fully described in our privacy policy and statement of California consumers' CCPA rights. Users must give their consent before iFunny, or any advertising SDK can process personal data consistent with local laws and app store policies. iFunny is also a signatory to the IAB Limited Service Provider Agreement, and FunCorp Ltd is an IAB-verified Consent Management Platform.
Our Investigation Findings
In response to Pixalate's article, FunCorp, and our two third-party experts, all parties mentioned thoroughly investigated iFunny's ad traffic and obtained feedback on iFunny's partners and clients. All of this confirmed what we had known all along: any purported fraudulent or illegal activity could only come from unscrupulous advertisers, and iFunny could not and did not generate the purported fraudulent ad traffic.
FunCorp's internal investigation identified several discrepancies between the claims made in Pixalate's article and how iFunny works. First, the malicious JavaScript mentioned in the article could have been provided and executed only through third-party SDKs. Second, after reproducing the malicious script and reapplying it to each step of our ad traffic, the script did not work as described in the article. Most notably, the script did not generate fake video ad traffic. This makes sense because even if the malicious script attempted to serve fraudulent video ads (using the standard VAST format cited by Pixalate), those attempts would fail. After all, we use WebView technology to display and measure advertisements incompatible with the VAST video ad format. To clarify how the scheme works, we have added our comments (in red) to the Pixalate diagrams below.
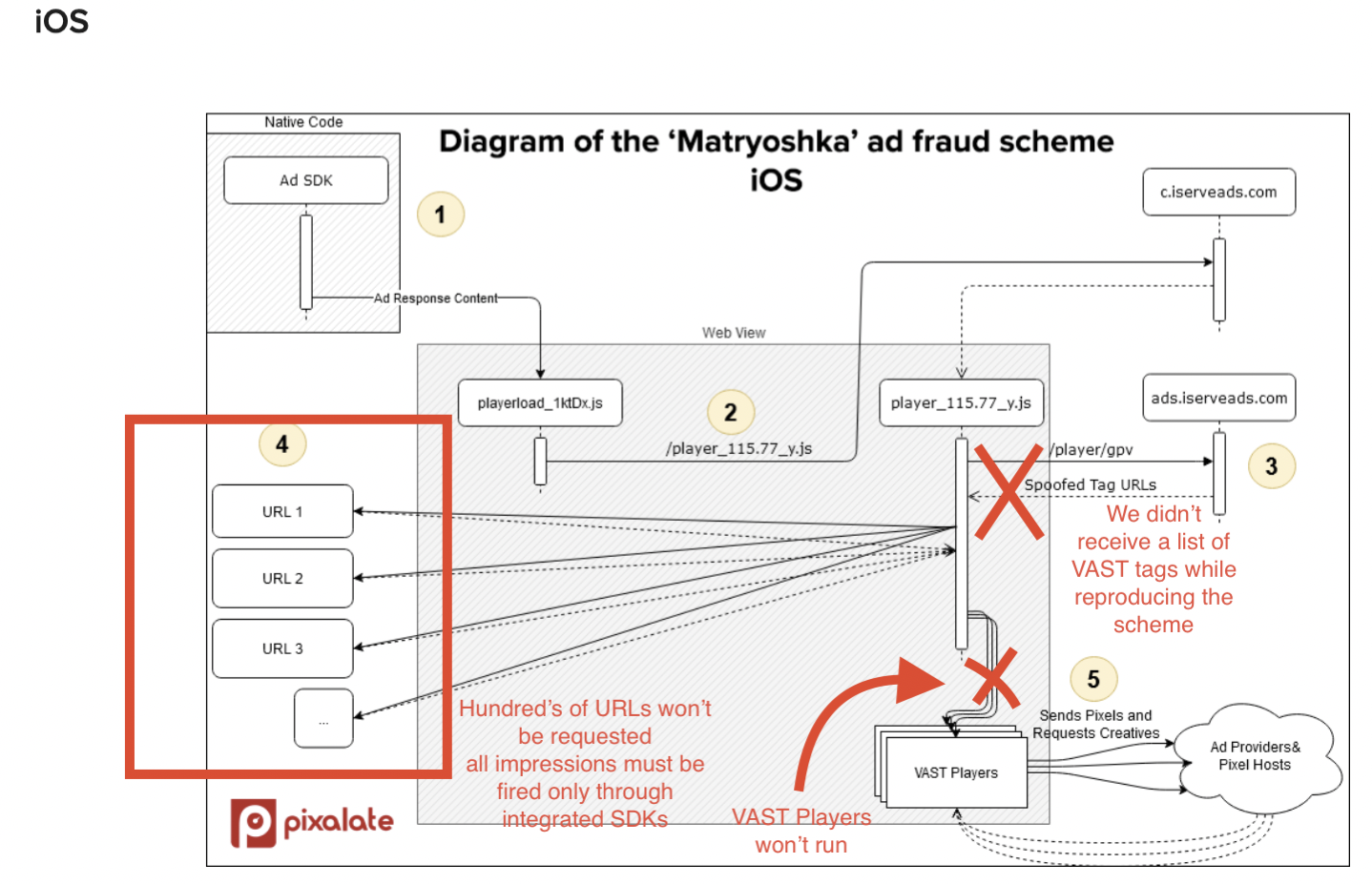
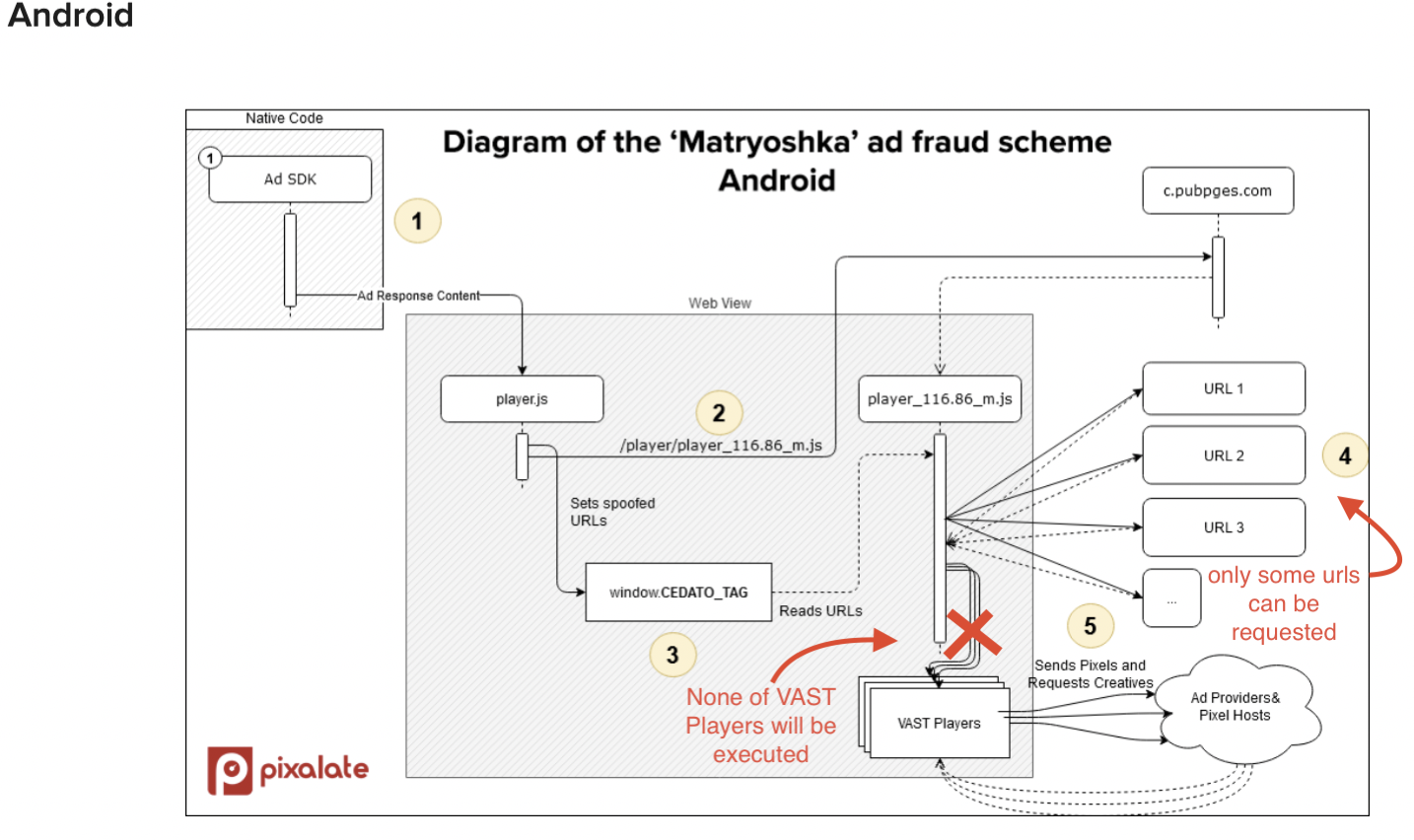
Similarly, it is unclear why Pixalate could not find the real source of the malicious JavaScript but alludes to involvement by iFunny. FunCorp has linked the malicious scripts to the domains identified in the chart below, none of which are related to iFunny.

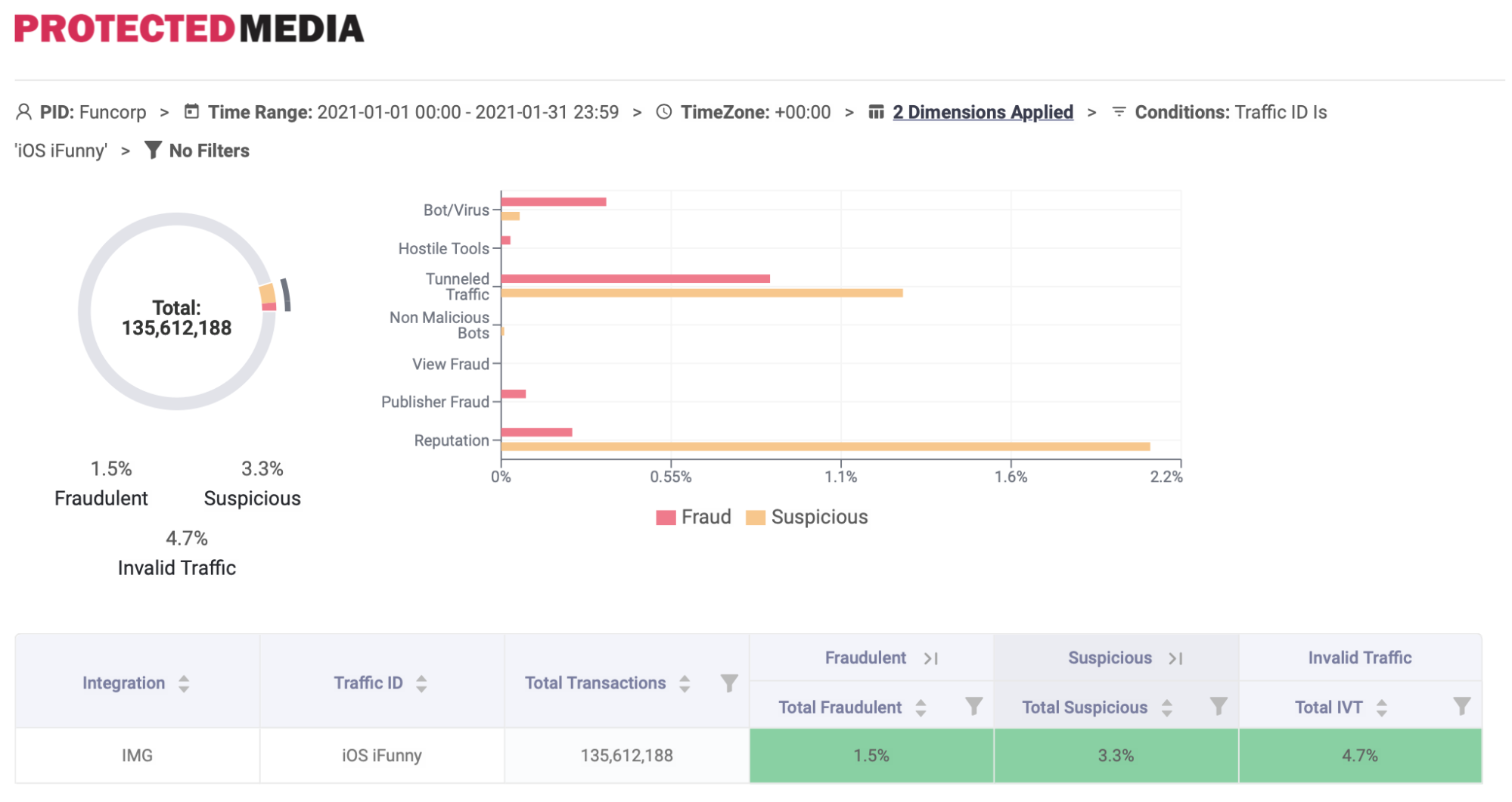
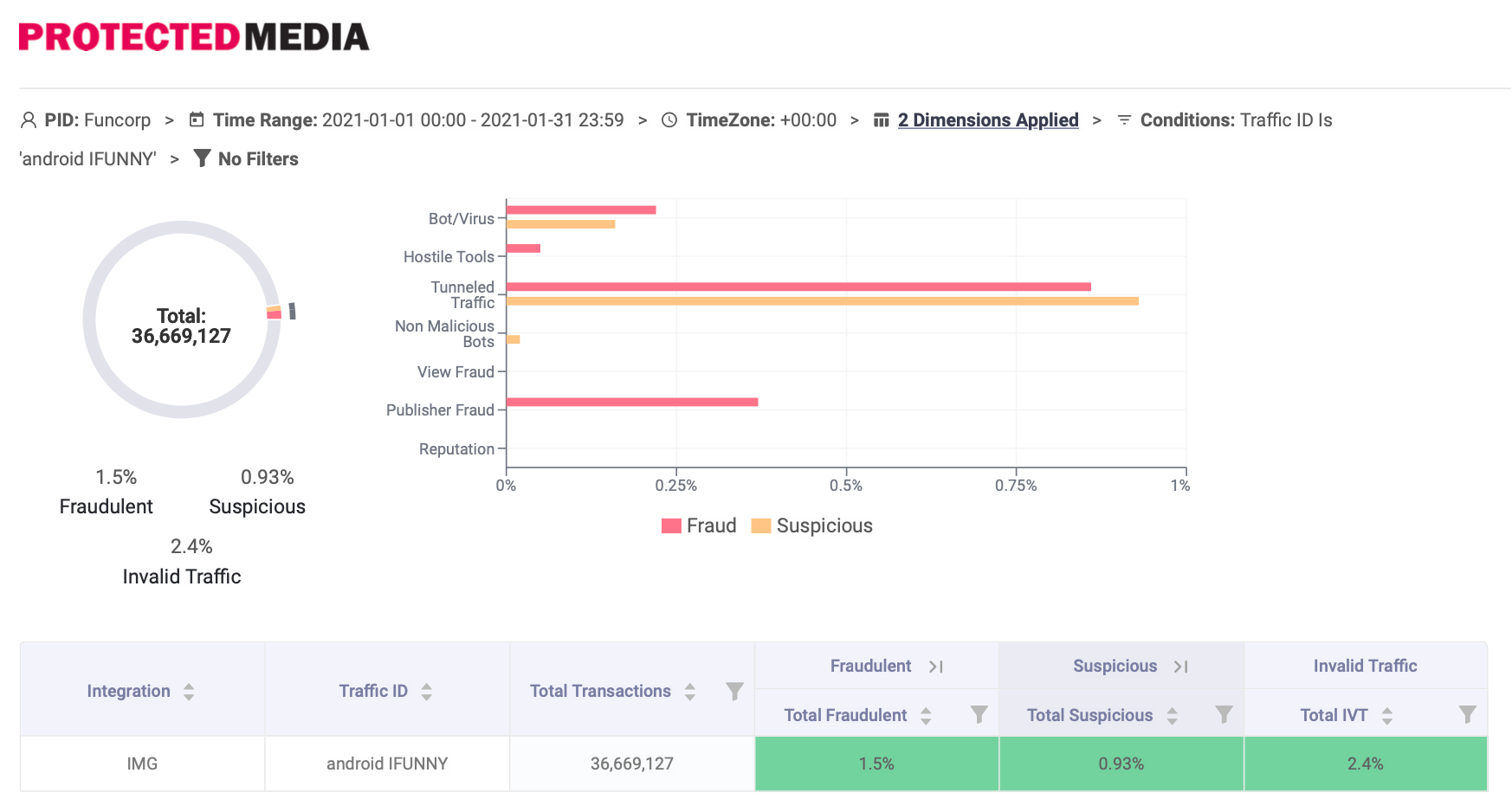
FunCorp also has the results of investigations of two independent, authoritative sources --- DoubleVerify and Protected Media. DoubleVerify's investigation concluded that "the fraudulent activity occurred on the demand side within the creative delivery" and that "there is no indication that iFunny participated in the scheme." Protected Media's investigation similarly concluded that FunCorp did not participate in any of the fraudulent activity. Specifically, Protected Media found close to zero percent of view fraud, bots, or publisher fraud; 98.5% of online traffic was irreproachable from any fraud activity. If any fraudulent activity was detected, it likely stemmed from the Tunneled Traffic category, in which the transactions can originate from private hosting providers or VPN usage that can produce false positives. The graphics below further detail Protected Media's findings.
iOS
Android
Numerous iFunny partners and clients have also confirmed that iFunny does not generate fraudulent ad traffic. In particular, MoPub, a Twitter company, our ad server, which has full access to iFunny's ad analytics, said the following:
"After an investigation into the issue, we did not find any evidence that iFunny was directly involved in the fraud scheme."
Other partners have expressed support for iFunny and our ad traffic practices:
-
"With confirmation from our global leading fraud protection partners, Fyber continues to see extremely low levels of IVT throughout recent months. FunCorp continues to be a trusted partner for Fyber, as it has been for years." - Fyber
-
"Upon investigating the issue both internally and with our fraud detection partners, we found no evidence of fraudulent activity on behalf of FunCorp nor that they were complicit in this attack." - PubMatic
-
"Based on our investigation we didn't observe fraudulent behavior for this traffic and our IVT vendors didn't detect traffic quality issue." -- Smaato
-
"As veterans and professionals in this industry who know all the 'in and outs' of the industry, we already understood and identified that FunCorp was not to blame for this fraudulent behavior. Our internal findings confirm that Funcorp's traffic exhibits low IVT levels." -- AcuityAds
-
"We trust you, and we believe there was no fraudulent action taken on your side. Your account will stay open with us." -- Inmobi
Our main bidding wrapper also finished its investigation of the case and regularly worked with us as a bidding wrapper and demand source.
We also implemented additional daily measures within our ad quality department to investigate suspicious transactions, including:
-
Improving our ads reporting system
-
Adding ad-related technical details into our internal analytics
-
Enhancing our alerting system, which allows us to react as quickly as possible to potential ad fraud
-
Controlling invalid traffic rates provided by Protected Media and thoroughly examining all marked creatives on our side.
There can be no dispute that iFunny did not partake in any ad fraud scheme and that it was third-party SDKs not affiliated with iFunny that were responsible for the purported ad fraud identified in the article. Nevertheless, as demonstrated by our swift and independently verified response to Pixalate's erroneous claims, we take all allegations of ad fraud seriously. FunCorp and iFunny remain wholly committed to safeguarding our users, partners, and clients and will continue to be vigilant by investigating and preventing ad fraud wherever possible.





